- Point of view
A crystal-clear view of third-party risk
How digital technologies create a robust risk framework

When a major retailer suffered a massive data breach because thieves stole its credentials from a third-party vendor, the consequences were severe. The event compromised over 40 million credit and debit card accounts and led to 140 lawsuits. Claims cost the company tens of millions of dollars and the breach badly damaged its reputation. Events like this – triggered by distributors, agents, joint-venture partners, contractors, and other third parties – are now common. Supply chains are growing longer and more complex. Meanwhile, regulators are extending their reach. Companies risk their reputations if they don’t establish comprehensive third-party risk management (TPRM) programs. But while most global enterprises recognize this, few have moved beyond stopgap solutions.
Today, third-party relationships have come under increased scrutiny. As multinational organizations continue to expand their operations around the world, they need safeguards against third-party risks. They must build a sustainable TPRM network that takes advantage of emerging technologies and advanced analytics.
But as organizations grow and mature, their portfolio of third and fourth parties swells. And collating data and screening an exhaustive database to spot risks quickly becomes more difficult. And they must do this while also meeting growing regulatory requirements, too.
Take a copy for yourself
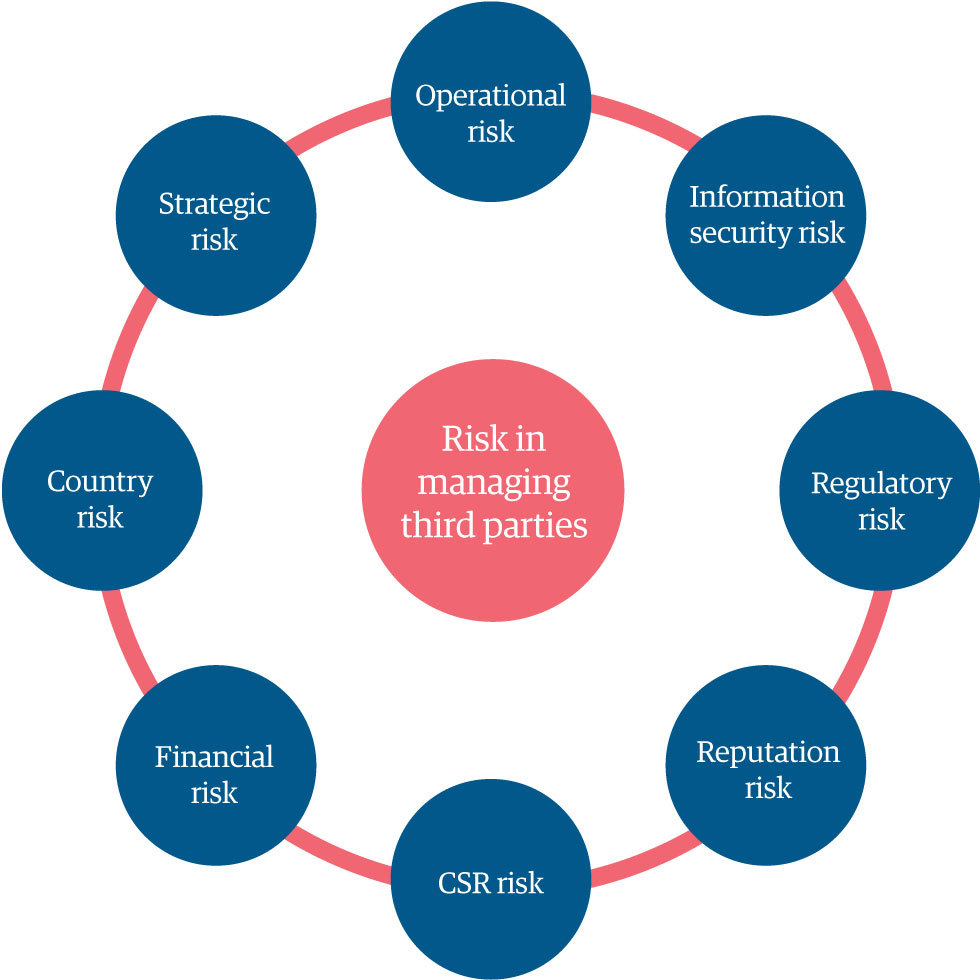
Hemmed in by myriad risks
Where do the risks that can threaten a firm’s financial and operational health come from? Figure 1 shows some key sources.
Here are important factors that underpin the need for TPRM:
- Pressure to reduce overall procurement costs means businesses rely on suppliers in emerging markets where corruption and illegal business practices are more prevalent
- Increasingly complex supply chains and supplier diversity are making accurate data interchanges essential; enterprises may also have less direct contact with their customers
- Third-party failures can trigger unpredictable – and potentially devastating – fines and operational losses
- Regulators are more aggressively enforcing frameworks such as the Foreign Corrupt Practices Act and guidelines from the Organization for Economic Cooperation and Development
- Social media has a powerful influence over consumer sentiment, calling greater attention to ethical practices in the supply chain
- Many investments in digital risk-management technologies aren’t delivering results – workflow or language processing tools, for example, are not fully aligned to business outcomes
Figure 1: Key sources of third-party risk
Thinking about the big picture
Although third-party risks are on the rise, many enterprises make do with an ad hoc, reactive approach to TPRM, leading to inefficient and incomplete outcomes.
Companies with in-house TPRM programs may have easy access to financial risk scores when screening suppliers. But they face real hurdles when it comes to non-financial risks that call for interpreting a large volume of data from both local and remote audits.
Bottom line: Many firms don’t have TPRM frameworks capable of managing risk across end-to-end business processes on a global scale. But they’re beginning to realize that this has to change.
Managing third-party risk end-to-end
Today, leading firms recognize the need for complete visibility of their upstream and downstream third-party risk exposure to anticipate, prevent, and manage adverse events. For proactive organizations, a third-party risk-assessment framework includes inherent risk-assessment methodologies, third-party due diligence, audits, financial risk assessment, continuous monitoring, and relevant mitigation strategies (see Figure 2).
Figure 2: A risk-management process enabled by digital technologies
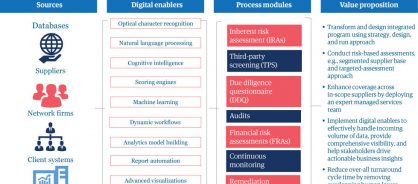
A holistic TPRM approach encompasses the following key processes:
- All-inclusive inherent risk assessment: Visibility over the complete third-party network is only getting harder to see as distinctions within the segments become less marked. The initial segmentation process of the third-party universe is based on key factors such as geographical risk, product risk, and spend category, among others.
- Best-in-class screening to cut through the noise: Cognitive computing, machine learning, and robotic automation can now interpret data from top global vendor-screening databases like LexisNexis, Dow Jones, and Thomson Reuters. This technology separates true hits from false positives and maintains an audit history to demonstrate due diligence. However, this does not replace the human element in the practice; it augments it, while improving efficiency and accuracy. This means that the layer of skilled risk professionals allows only relevant red flags to be reported, enabling appropriate, focused action.
- Enhanced due diligence for targeted action: Improving the depth and scope of risk assessments is equally important. And this is where enhanced due diligence assesses high-risk suppliers for geographic, information security, social, ethical, and environmental risks. Digital technologies, such as natural language processing, workflow tools, and advanced analytics, can make it easy to analyze, score, and aggregate results across a region or around the world.
- Audits that direct resources where they're needed most: The right combination of on-site and remote-site audits is key to reducing assessment cycle times and rapidly formulating action plans. This balance has become essential as cost-cutting pressures push supply chains out to suppliers whose negatives ad hoc approaches may miss. Digital can help solve this puzzle by focusing limited resources on situations and geographies where the risks are greatest.
- Assessment of the financial impact and likelihood of risk: Financial risk assessments determine whether a company is operating within its stated risk appetite and is performing within accepted financial parameters. This analysis answers an important question: How big an impact would this risk have if it were to occur? The impact should be considered, taking into account the mitigating impact of the risk controls and the monitoring of risk controls.
- Targeted action to limit damage or prevent it altogether: To take corrective and preventive action, you need targeted remediation plans. These plans have to consider complex parameters such as a firm's risk appetite or how critical a given vendor is. This may mean having a strategy for working with the vendor to improve processes or, as a last resort, ending the relationship.
- Robust continuous monitoring and periodic screening: With access to compliance databases and tools, an automated process of keeping a periodic or event-driven eye on red flags for high-risk third parties has helped risk managers stay abreast of compliance and risk issues associated with a third party's regulatory and operational environment.
Visit our enterprise risk and compliance services page
Integrating these processes into a cohesive whole can be a challenge, but a comprehensive program with deep risk expertise can help. Take a holistic TPRM approach rather than focusing on quick wins or discrete fixes. The result: simple transformation that requires few changes.
Case studies
Better supplier compliance, sustainable sourcing
A global consumer goods company increased risk coverage from 5,000 suppliers to 50,000 suppliers, and identified 135 high-risk and 275 medium-risk suppliers. It significantly helped the procurement function reduce the risk of regulatory non-compliance.
Stamping out risk from corrupt suppliers
A footwear and clothing manufacturer ran an end-to-end screening process with built-in data analytics to assess the company's existing network of third parties in high-risk territories. The company identified more than two dozen potentially problematic third parties, reduced the risk of regulatory penalties, and gained greater protection from reputational damage.